AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. AWS CloudTrail is a service that you can use to capture information about the API actions happening in your AWS account, AWS SDKs, command line tools, and other AWS services.
What is CloudTrail?
Why Use CloudTrail?
Here are some key reasons to use CloudTrail:
CloudTrail Log Files
The log files capture API activity from all Regions and are delivered every 5 minutes. You can easily search and analyze the logs using Amazon Athena, Amazon Elasticsearch, and other tools.
CloudTrail Events
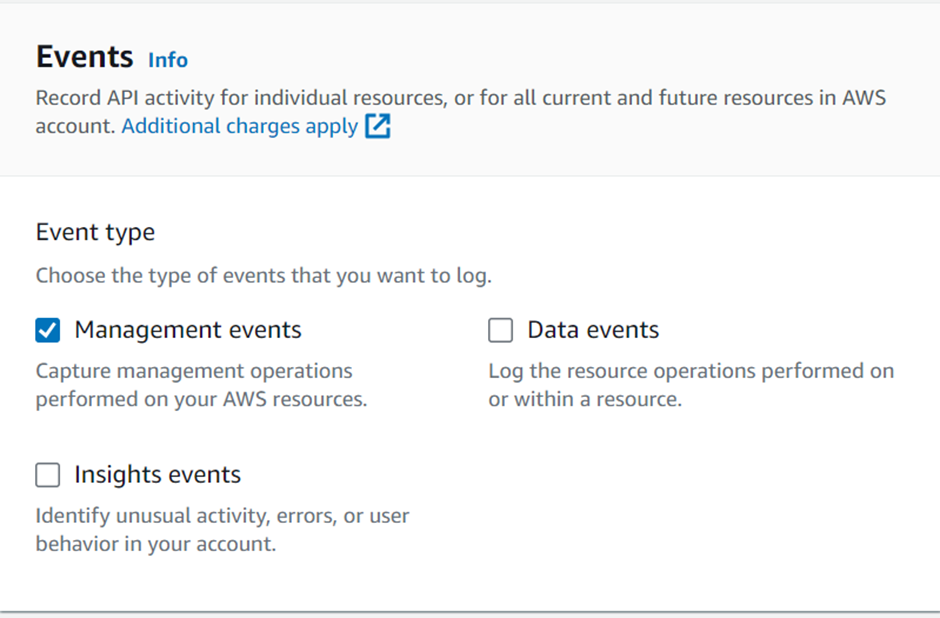
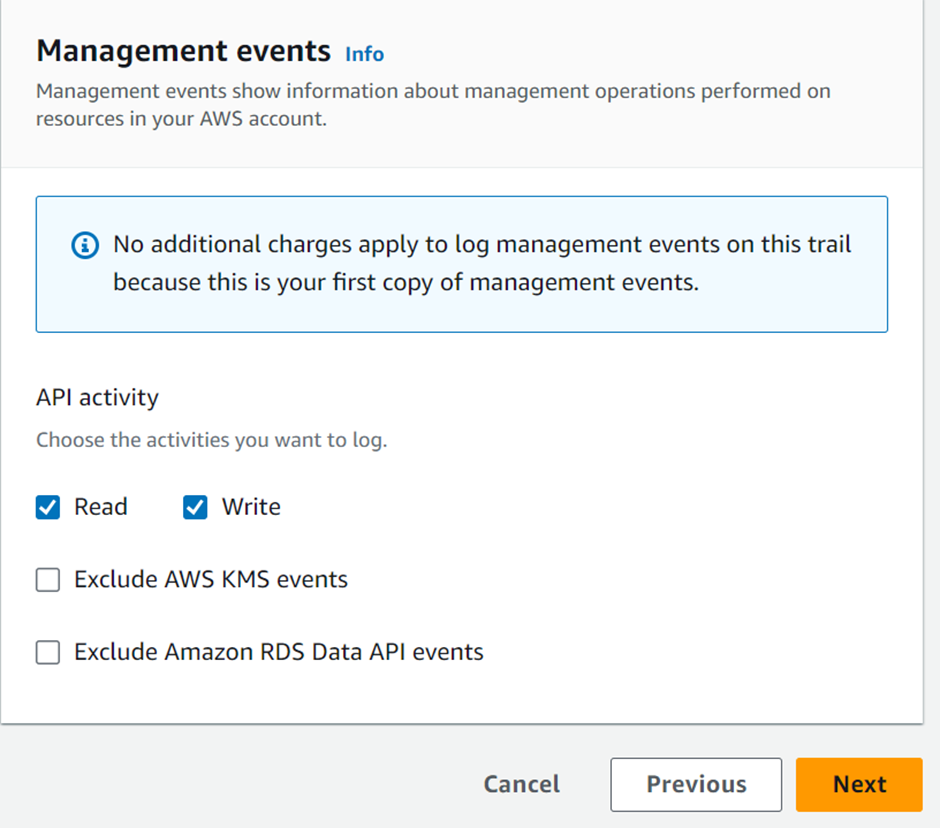
Management events
Data events
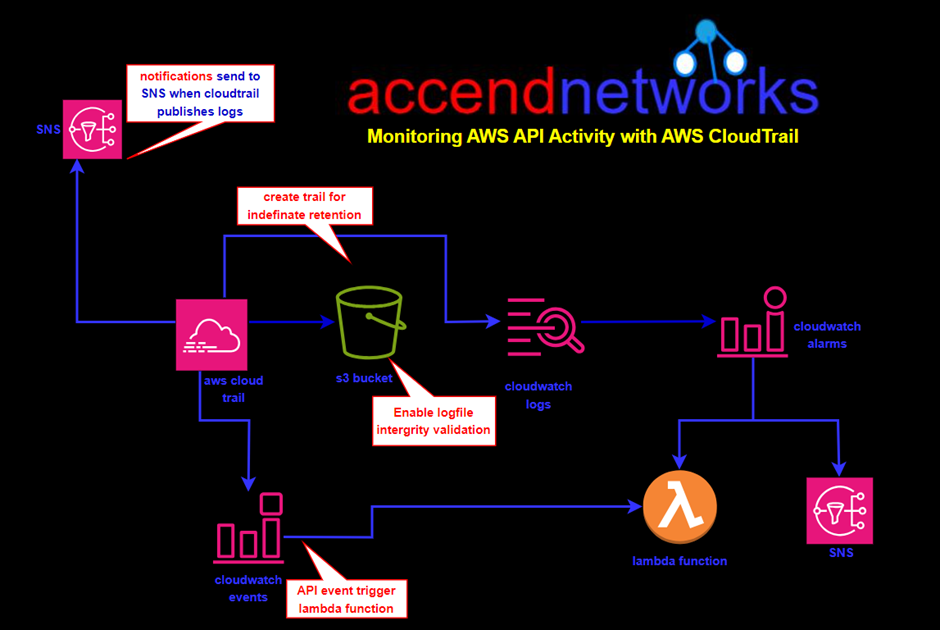
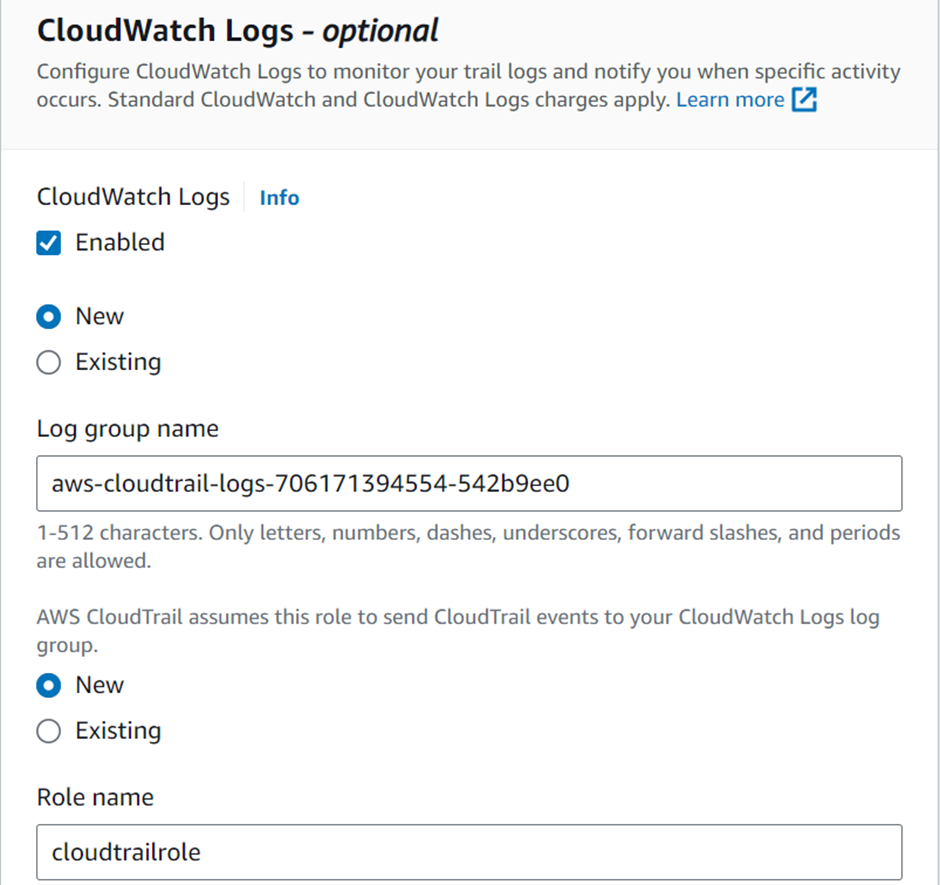
By default, AWS logs and retains management events for a period of 90 days. but this timeframe might need to be revised for your requirements. To overcome this, you can create a CloudTrail trail, enabling you to log events in S3 for indefinite retention. Each trail you create can be region-specific or it can be applied to all regions. Furthermore, you can leverage CloudWatch events to trigger actions based on API calls that are made and logged in CloudTrail.
Using information generated by CloudTrail.
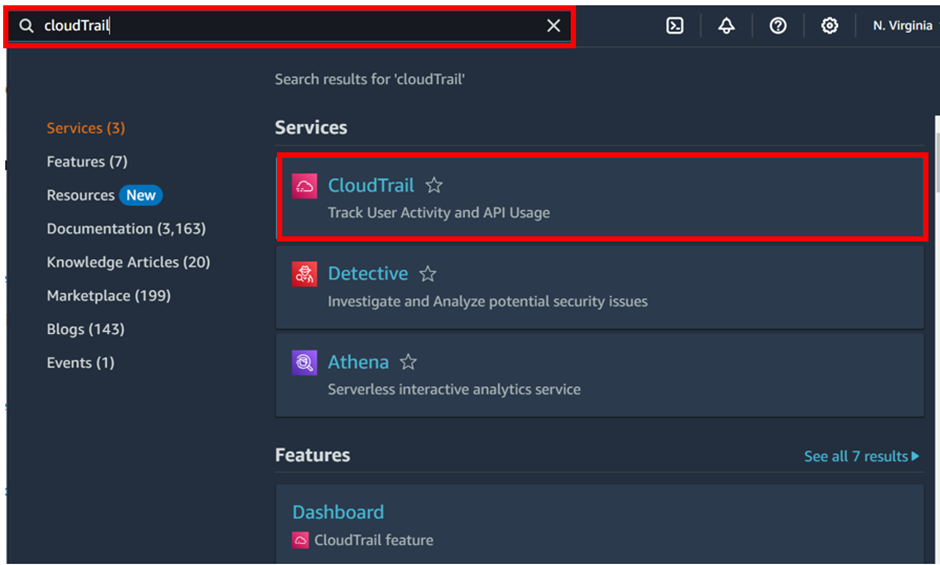
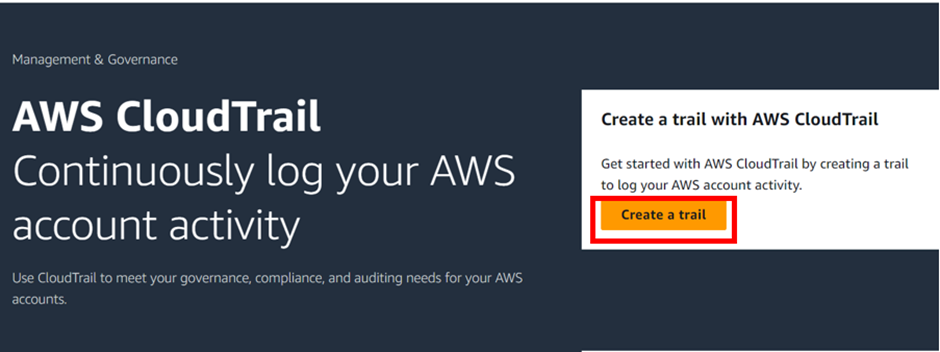
Hands-on creation of CloudTrail trail.
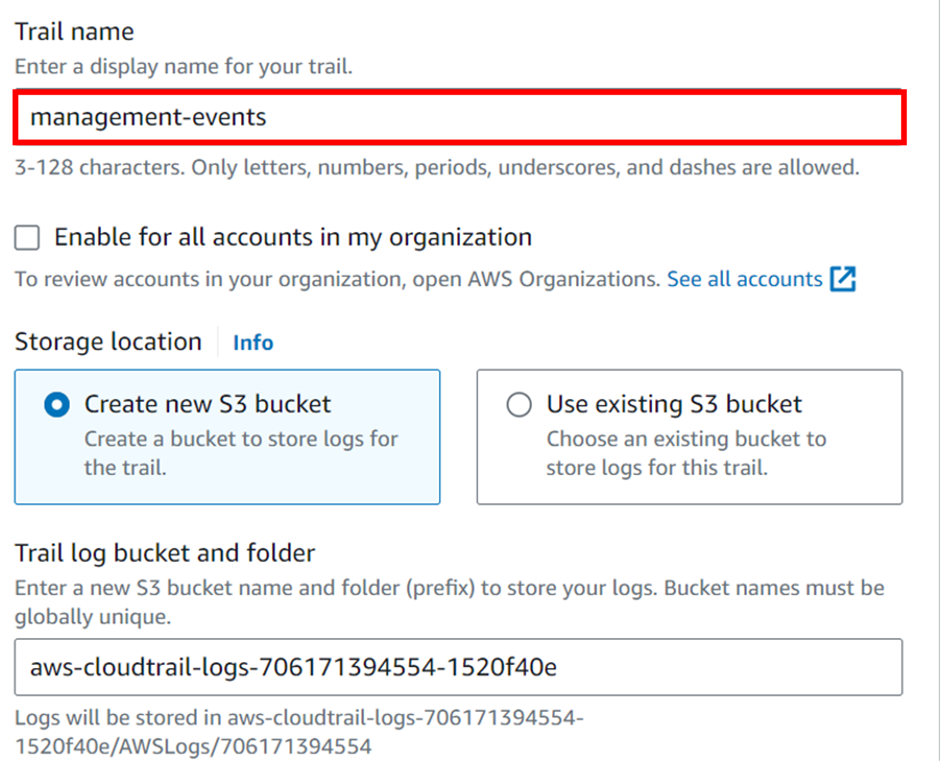
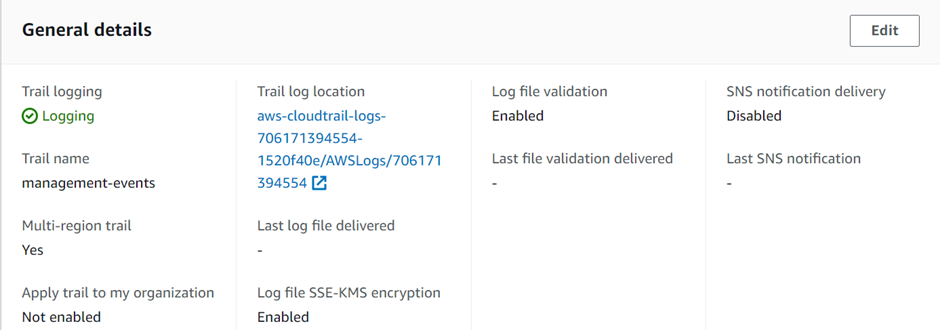
It’s going to need a storage location, and by default, it will create an S3 bucket. And give it a unique name. So, we will leave that as the default.
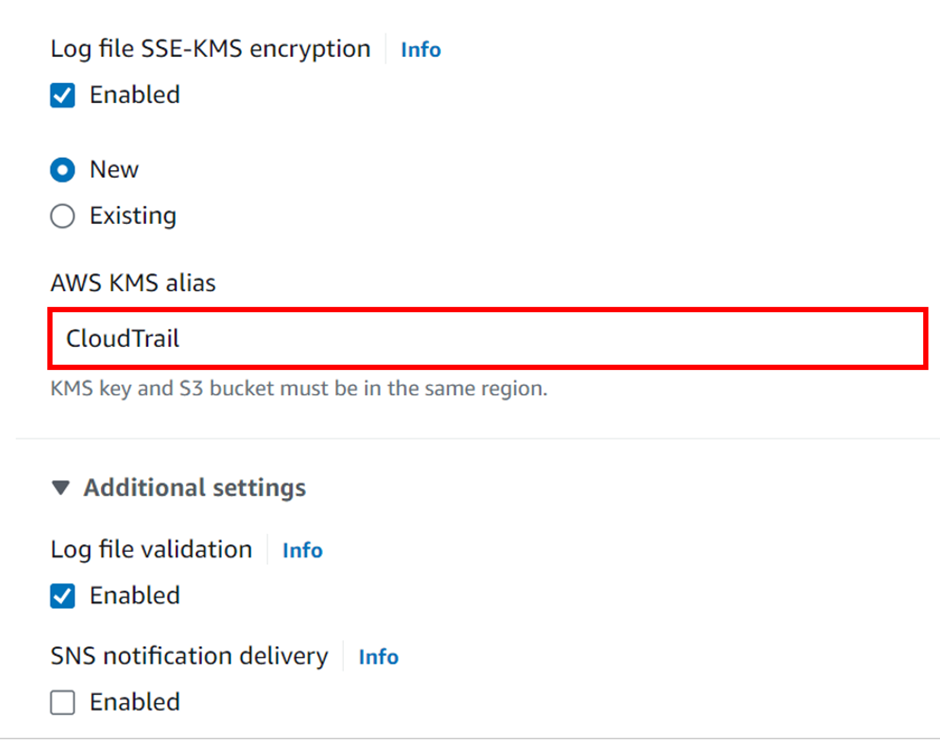
Logfile validation is enabled by default Scroll down.
This brings us to the end of this blog. Cleanup.
Stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you!

















