What is Amazon Inspector?
Amazon Inspector automatically discovers workloads, such as Amazon EC2 instances, containers, and Lambda functions, and scans them for software vulnerabilities and unintended network exposure.
How it works.
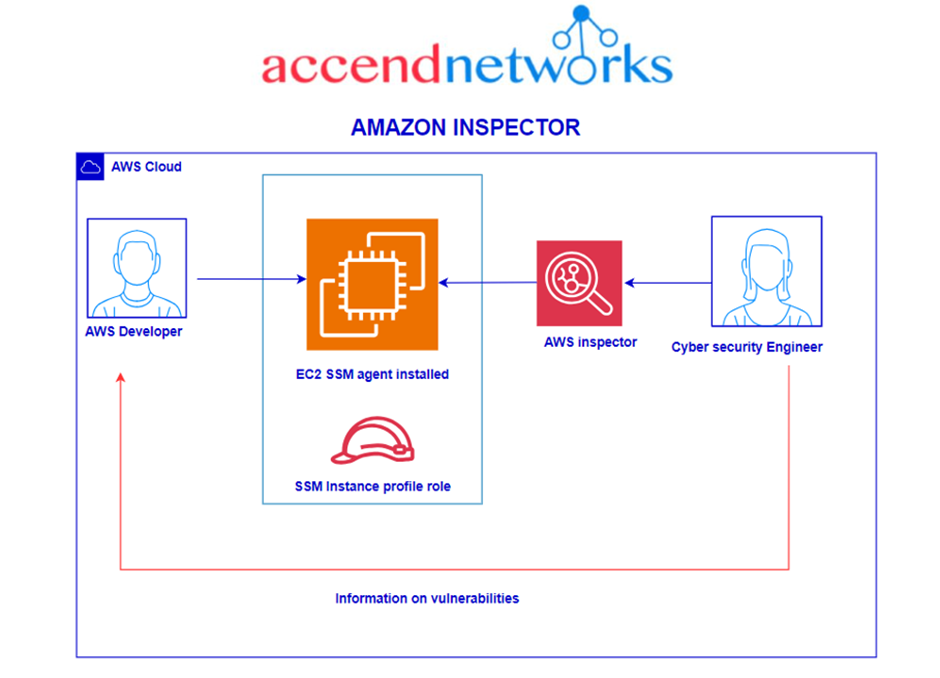
Amazon Inspector is an automated vulnerability management service that scans AWS workloads for software vulnerabilities and unintended network exposure. At a high level, AWS Inspector is dependent on an SSM agent to be installed in the EC2 instance that will be used to scan and report the security findings. Additionally, the EC2 will need a role that grants SSM to the EC2 instance. AWS Inspector uses the SSM agent to connect to the instance. Note that as of November of 2023, there is a new agentless scan option that is in preview.
AWS Inspector can be supported at the organizational level and scan all accounts in the organization; however, the scope of this blog will be a single account.
In this use case, we will see how Amazon Inspector helps to identify the network vulnerability by performing an accessibility check.
Let’s proceed as follows.
Login to your AWS account using your admin account or an account with admin privileges.
Creation of a new IAM role for the EC2 use case
Remember, the AWS Inspector is dependent on an SSM role or a role with SSM permissions to be able to communicate with the SSM agent inside the EC2. Let’s create this role.
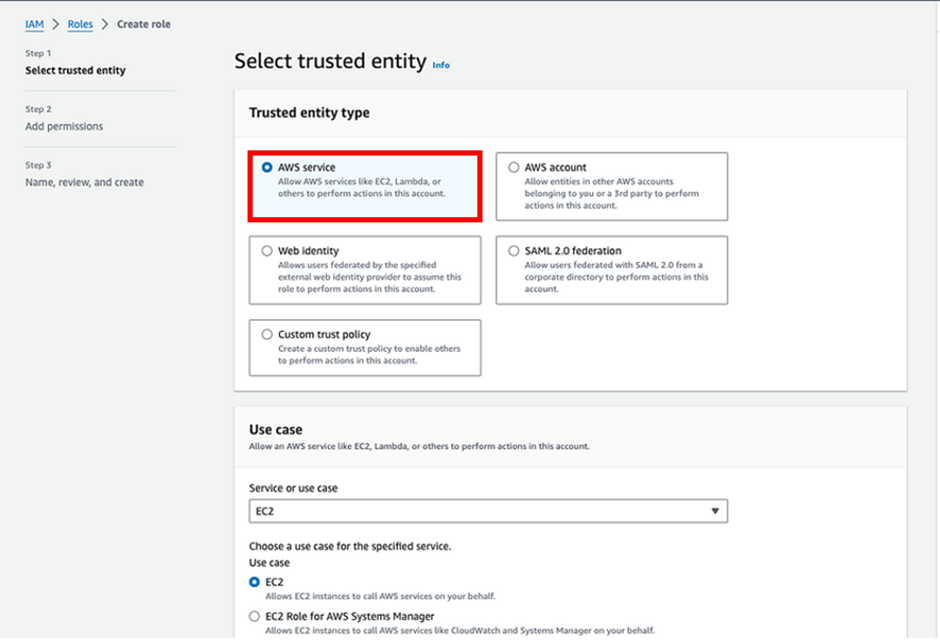
Navigate to IAM, click on Roles then click on the Create role button. You will be prompted to select an entity type, in our case select “AWS service”, and for service select EC2. This will create a trust policy that will allow EC2 to assume it. Click Next.
Now we must add permissions to the role that the EC2 will assume. Under the Add permissions config screen, search for AmazonSSMManagedInstanceCore, select it, and click Next.
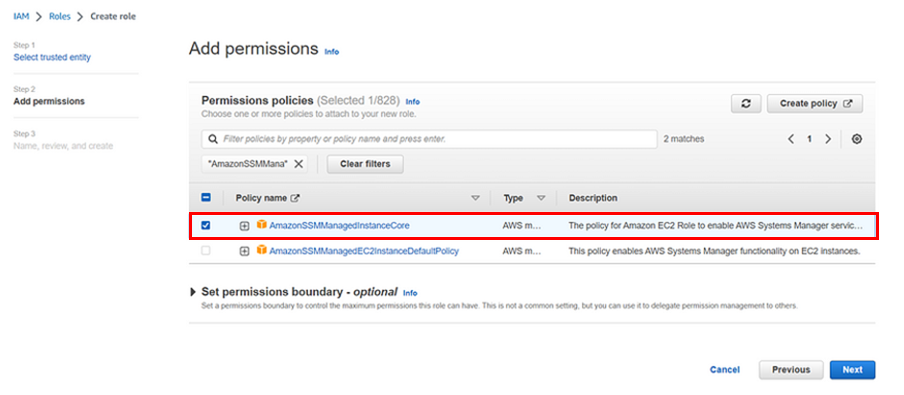
In the next window, give the role a name (SSMRoleForInspector) and click Create role.